This Citibank Phishing Scam Could Trick Many People
January 21: A new Citibank phishing scam is underway that utilizes a convincing domain name, TLS certs, and even requests OTP codes that could easily cause people to believe they are submitting their personal information on a legitimate page.
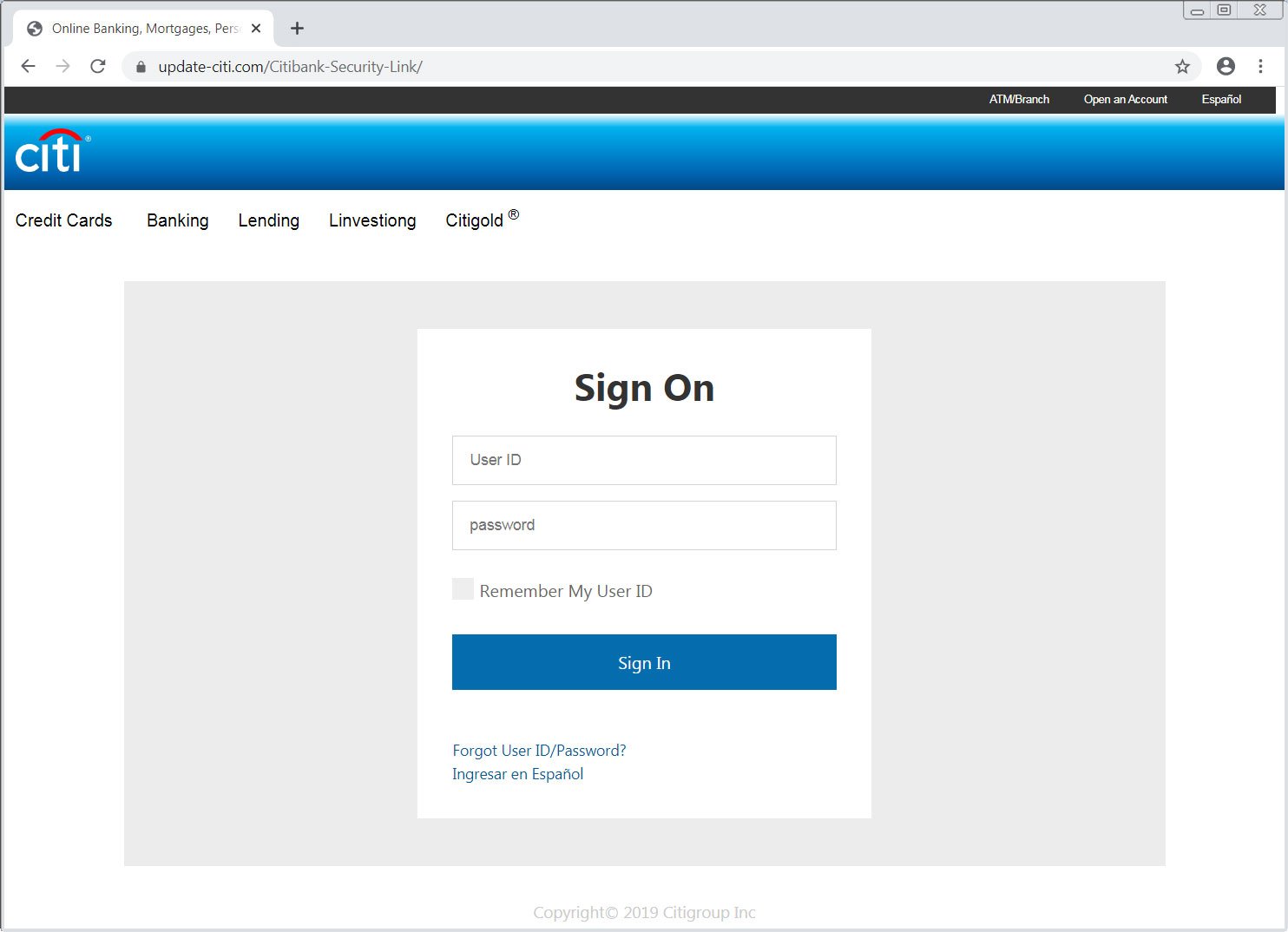
It is not known how users arrive at this phishing site, whether it be from an email or SMS text, but when they visit the update-citi .com landing page found by MalwareHunterTeam, they will be presented with a convincing Citibank login page.
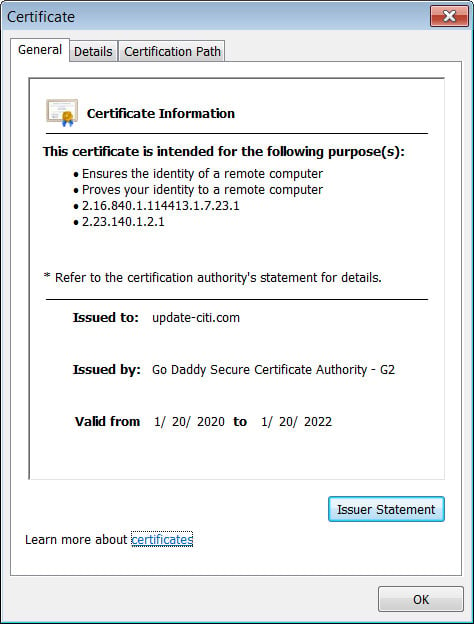
This fake Citibank site also utilizes a TLS certificate for the domain so that a lock appears next to the address. While this should not make a web site appear more legitimate as it only means submitted data is encrypted, for many users a lock symbol tends to lend authenticity to a page.
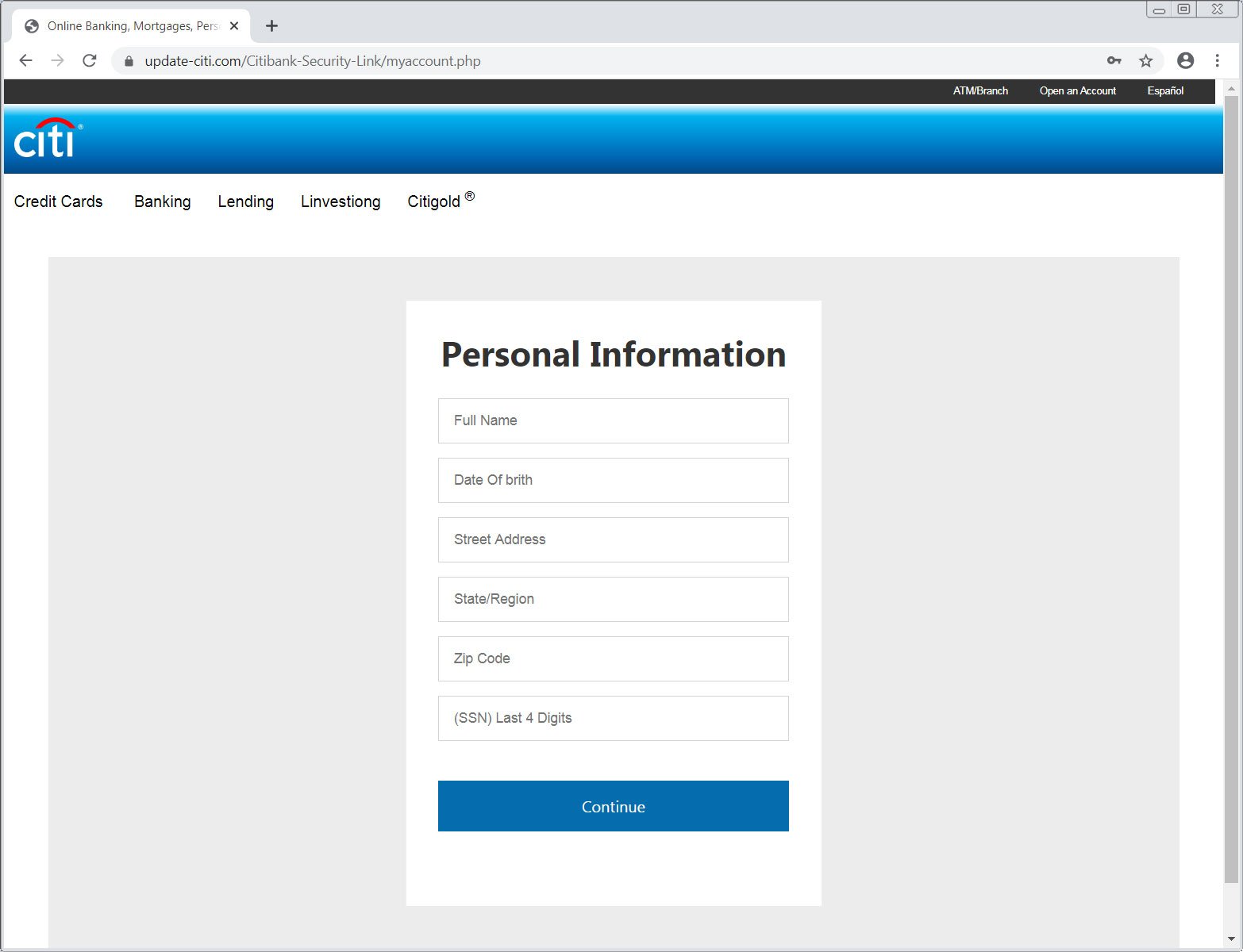
When a user enters their login information into the phishing site, they will be presented with various forms that request personal information from the victim. This includes the full name, DOB, address, and their last four digits of their social security number and their debit card number, debit expiration date, and security code.
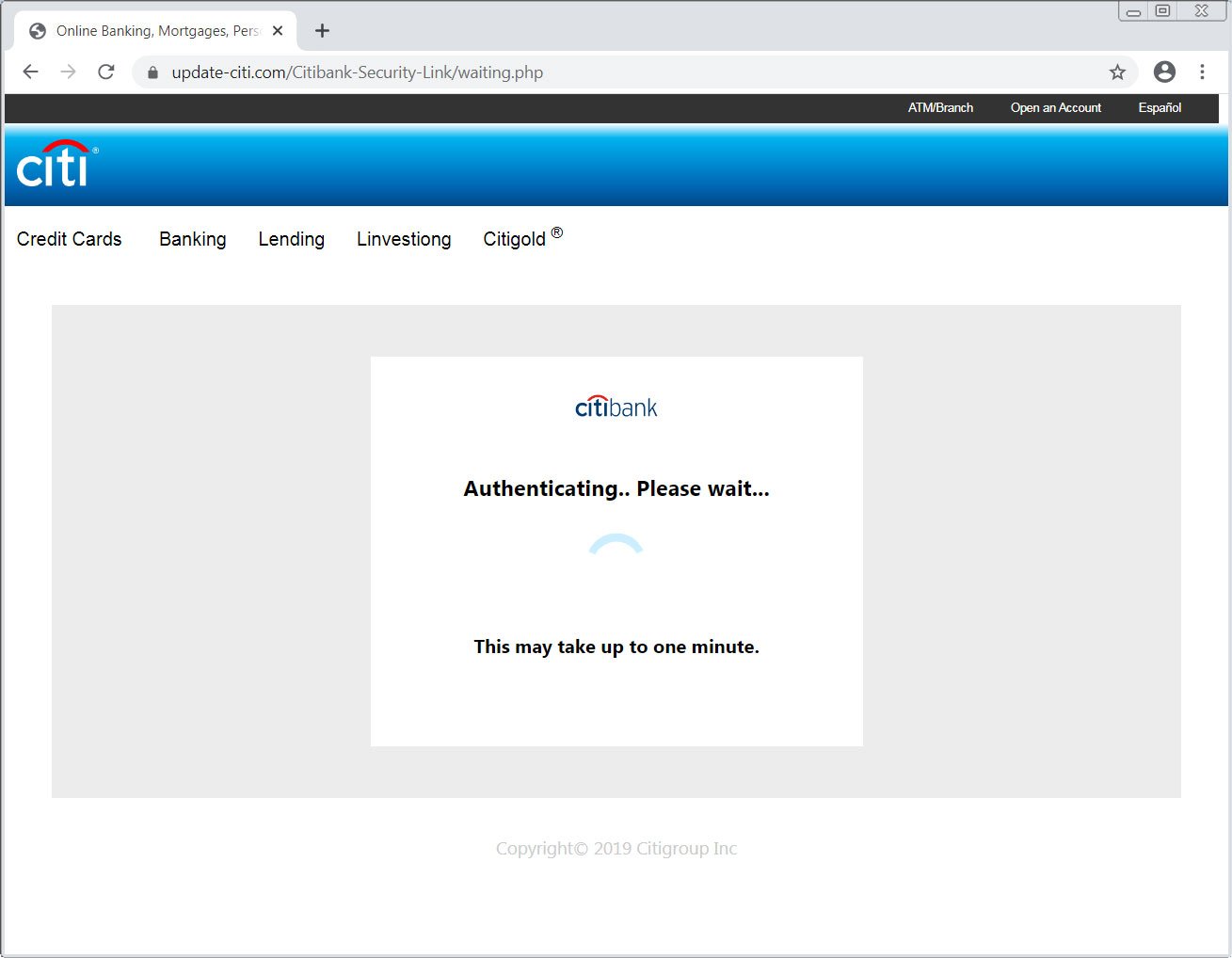
Each page of information that is entered will be submitted to the attacker’s server and when done, the landing page will state it is authenticating your data. This process can take upwards to a minute to complete.
It is believed, but not confirmed, that during this period the phishing page will attempt to login to Citibank using the credentials provided by the victim. This is done in the background similar to this Steam phishing scam.
If the phishing site does indeed login to the Citibank account and a user has an OTP (One-Time PIN) authentication configured on their account, it will trigger Citibank to send the code to the victim’s cell phone number.
As this code will be sent from Citibank’s servers, it further lends authenticity to the phishing site.
After the above delay, the phishing page then asks the victim to enter their OTP to continue.
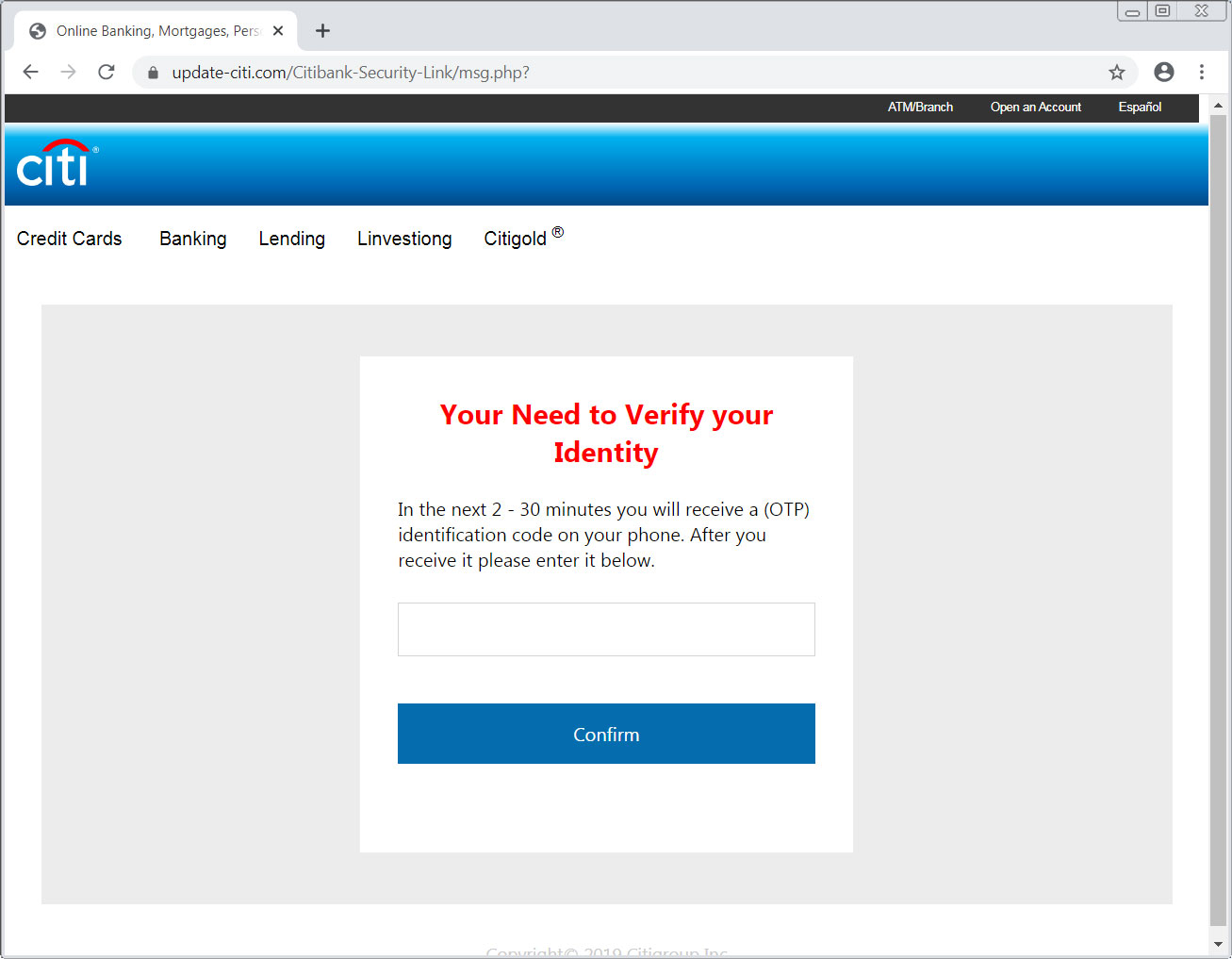
Szabolcs Schmidt, a security professional in the European banking industry, has told BleepingComputer that he has never seen an online bank phishing site triggering OTP codes via SMS and then requesting them from the victim.
Once the attackers have access to the victim’s personal information, debit card information, and the OTP code, they can now login to the victim’s account and take full control over it.
This could allow malicious activity such as the stealing of money, changing the address on the account, or even opening other accounts under their name.
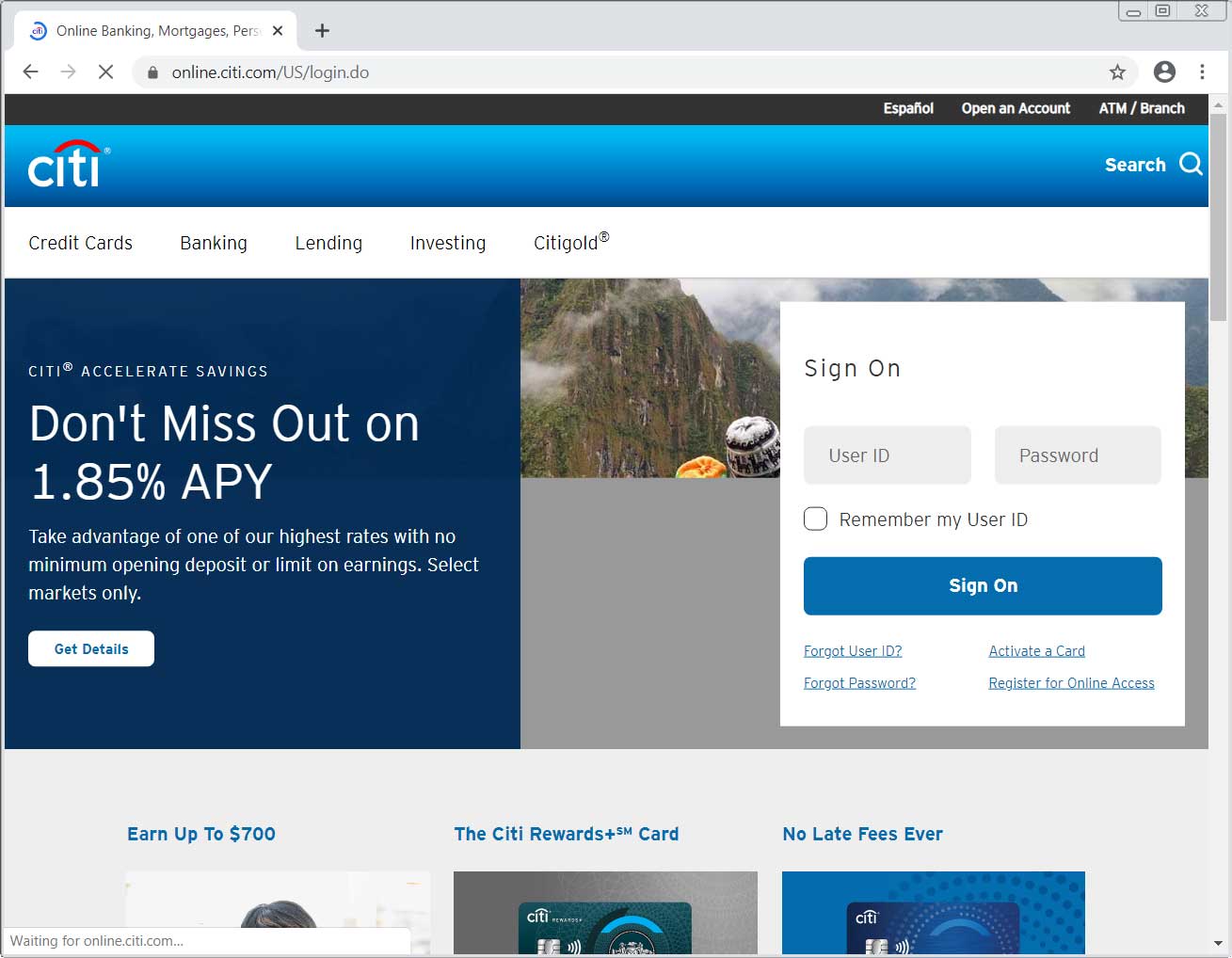
Now that the victim has been squeezed dry of all necessary information, the phishing landing page will redirect the user back to the legitimate Citibank login page and leave the user unsure as to what happened.
Phishing scams are becoming more intricate day-by-day by using convincing domains and automated procedures.
Due to this, everyone must pay close attention to the URLs that they submit their personal information. If it does not match the URL for their bank, they should not enter their information and go directly to the legitimate site when logging into their account.

